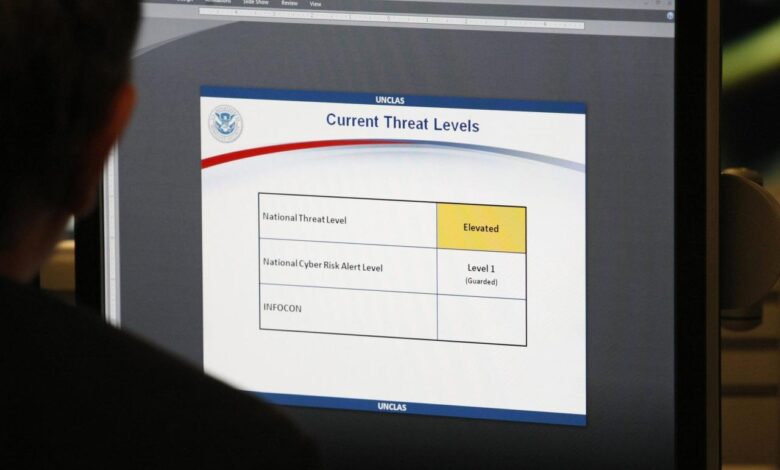
FBI Warns: Chinese Hackers Targeting US Critical Infrastructure
Chinese hackers determined to wreak havoc on us critical infrastructure fbi warns – The FBI has issued a stark warning, alleging that Chinese hackers are actively targeting US critical infrastructure with the intent to wreak havoc. This alarming revelation raises serious concerns about the vulnerability of our nation’s essential systems to cyberattacks. The potential consequences of a successful attack could be devastating, ranging from widespread power outages and communication disruptions to disruptions in essential services like healthcare and transportation.
The FBI’s warning underscores the urgent need to bolster our cybersecurity defenses and implement proactive measures to mitigate the risks posed by these sophisticated cyber threats.
This alarming situation demands a thorough examination of the methods employed by Chinese hackers, the vulnerabilities they exploit, and the motivations driving their actions. We must understand the specific sectors of critical infrastructure most vulnerable to cyberattacks, and the potential impact of successful attacks on each sector.
By delving into these critical aspects, we can develop effective mitigation and defense strategies to protect our critical infrastructure from these persistent threats.
Chinese Hacking Activities: Chinese Hackers Determined To Wreak Havoc On Us Critical Infrastructure Fbi Warns
Chinese hackers have been actively targeting US critical infrastructure for years, posing a significant threat to national security and economic stability. These actors employ sophisticated techniques to infiltrate systems, steal sensitive data, and disrupt operations, often with the aim of gaining a strategic advantage or undermining US interests.
Methods and Tactics
Chinese hackers utilize a diverse range of methods and tactics to penetrate critical infrastructure systems.
- Exploiting Vulnerabilities:Hackers often exploit known vulnerabilities in software, hardware, and network configurations to gain unauthorized access. These vulnerabilities can range from unpatched security flaws to misconfigured devices.
- Social Engineering:Hackers use social engineering tactics, such as phishing emails or phone calls, to trick individuals into providing sensitive information or granting access to systems.
- Malware Deployment:Chinese hackers deploy malicious software, such as ransomware or spyware, to steal data, disrupt operations, or gain persistent access to systems.
- Advanced Persistent Threats (APTs):APTs involve long-term, targeted attacks that aim to infiltrate and maintain access to systems over extended periods.
These campaigns often leverage custom-built malware and sophisticated techniques to evade detection.
- Insider Threats:Hackers may also target individuals with access to critical infrastructure systems, seeking to exploit their credentials or influence them to provide access.
Examples of Exploited Vulnerabilities, Chinese hackers determined to wreak havoc on us critical infrastructure fbi warns
Chinese hackers have exploited a wide range of vulnerabilities in US critical infrastructure systems, including:
- Industrial Control Systems (ICS):Hackers have targeted ICS vulnerabilities, such as those found in SCADA systems used in power plants, water treatment facilities, and pipelines.
- Internet of Things (IoT) Devices:Chinese hackers have exploited vulnerabilities in IoT devices, such as smart meters and industrial sensors, to gain access to critical infrastructure networks.
- Software Supply Chain:Hackers have targeted software supply chains, compromising software development tools or code repositories to inject malware into widely used software.
- Cloud Computing Platforms:Chinese hackers have targeted cloud computing platforms, seeking to gain access to sensitive data or disrupt cloud-based services.
Motivations
Chinese hacking activities targeting US critical infrastructure are driven by a complex mix of motivations, including:
- Economic Espionage:Chinese hackers often seek to steal intellectual property and trade secrets, providing economic advantages to Chinese companies.
- Strategic Advantage:Chinese hackers may aim to gain a strategic advantage by disrupting critical infrastructure, impacting US economic and military capabilities.
- Political Influence:Chinese hackers may seek to influence US political discourse or undermine US foreign policy through cyberattacks.
- Cyber Warfare:Chinese hackers may conduct cyberwarfare operations, targeting US critical infrastructure to disrupt or damage essential services.
- Intelligence Gathering:Chinese hackers may seek to gather intelligence on US critical infrastructure systems, providing insights into vulnerabilities and potential targets.
Final Summary
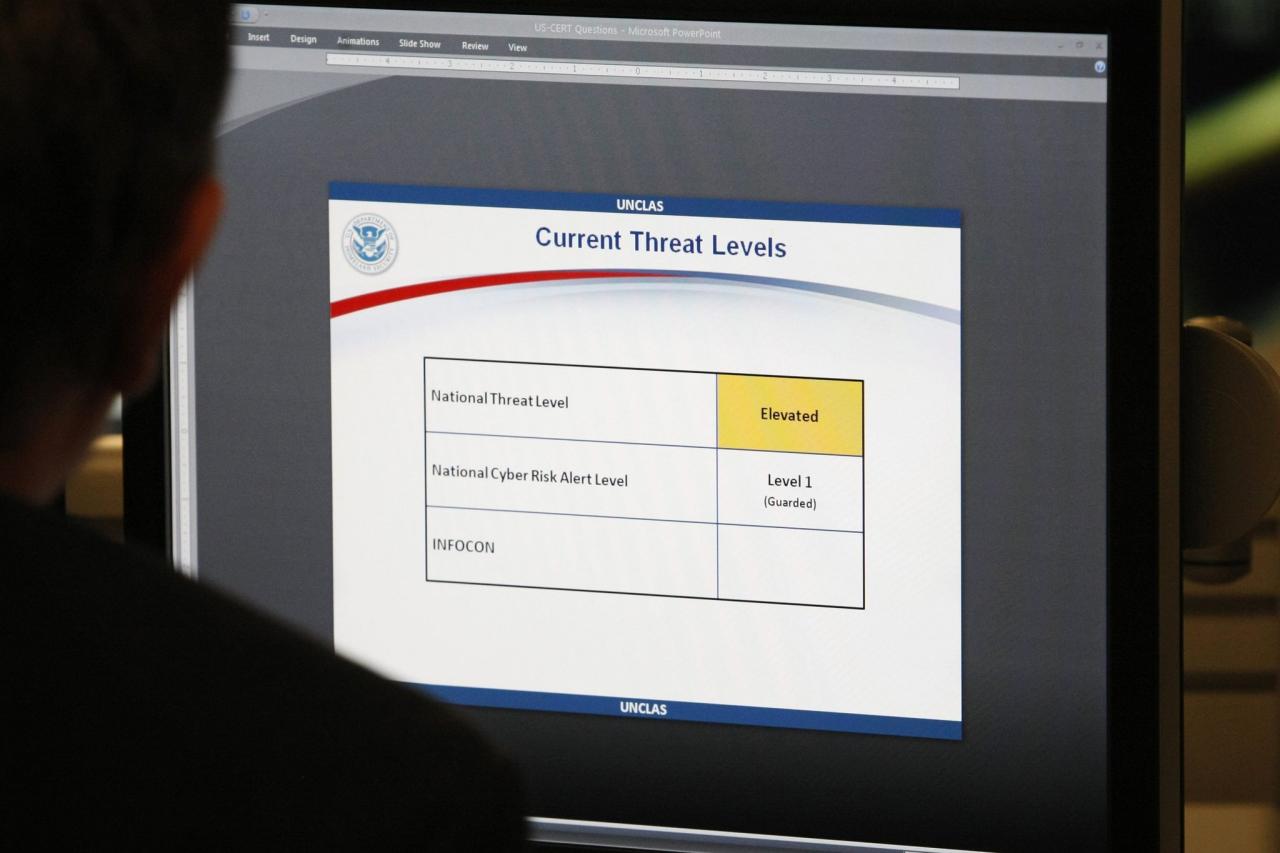
The FBI’s warning about Chinese hackers targeting US critical infrastructure serves as a wake-up call, highlighting the urgent need for a multifaceted approach to cybersecurity. Strengthening our defenses, fostering international cooperation, and raising public awareness are crucial steps in mitigating these risks.
By working together, we can bolster our cybersecurity posture and safeguard our critical infrastructure from the growing threat of cyberattacks. The stakes are high, and we must act decisively to protect our nation’s security and well-being.
The FBI’s warning about Chinese hackers targeting our critical infrastructure is a sobering reminder of the threats we face in the digital age. It’s a stark contrast to the inspiring story of Aisam-ul-Haq Qureshi, who is motivated by the rise of his Davis Cup teammate Rohan Bopanna, as seen in this recent article.
While the world grapples with cyber threats, the spirit of sportsmanship and friendly competition reminds us that there’s still hope for collaboration and mutual respect on the global stage. Hopefully, the lessons learned from the sporting world can translate into a more secure digital future for all.
It’s unsettling to hear about Chinese hackers targeting our critical infrastructure, especially given the FBI’s warnings. It’s a reminder that even as companies like Toyota raise their annual net profit forecast as the chip shortage eases , there are still significant threats to our national security.
We need to stay vigilant and prioritize cybersecurity measures to protect our vital systems from these malicious actors.
It’s a strange world we live in, where the FBI warns of Chinese hackers targeting our critical infrastructure while, on the other side of the globe, a young widow who gained fame as an influencer is among the few women running for office in Pakistan.
This story is a reminder that even in the face of global threats, there are individuals fighting for change and representation. The fight against cybercrime is just one aspect of the complex challenges we face, and it’s important to remember that the world is full of stories of resilience and hope.

